Netflow Compromise Network Infrastructure Device
Sometime ago, I was involved in a short project where a particular data-center was unavailable (or access was very slow). Our task was to find out what the problem was and fix it as soon as possible being a critical data-center.
Since we could not access the devices, we could not perform on-the-spot troubleshooting.Thankfully, the organization had been monitoring (and keeping logs of) all traffic going through the data-center and from their Cisco Devices. After combing through the logs, we found the problem (a denial of service attack) and restored access to the data-center.Troubleshooting is one of the reasons to perform monitoring on your network as evident from that personal story. Other reasons include:.: Is your ISP being sneaky or is a worm is eating up your bandwidth?. Performance monitoring: Monitoring can help you determine if your network is performing optimally or if there is network congestion (e.g.
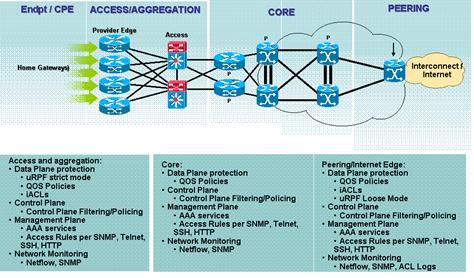
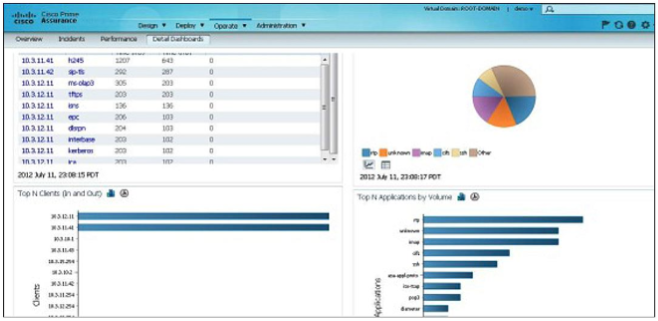
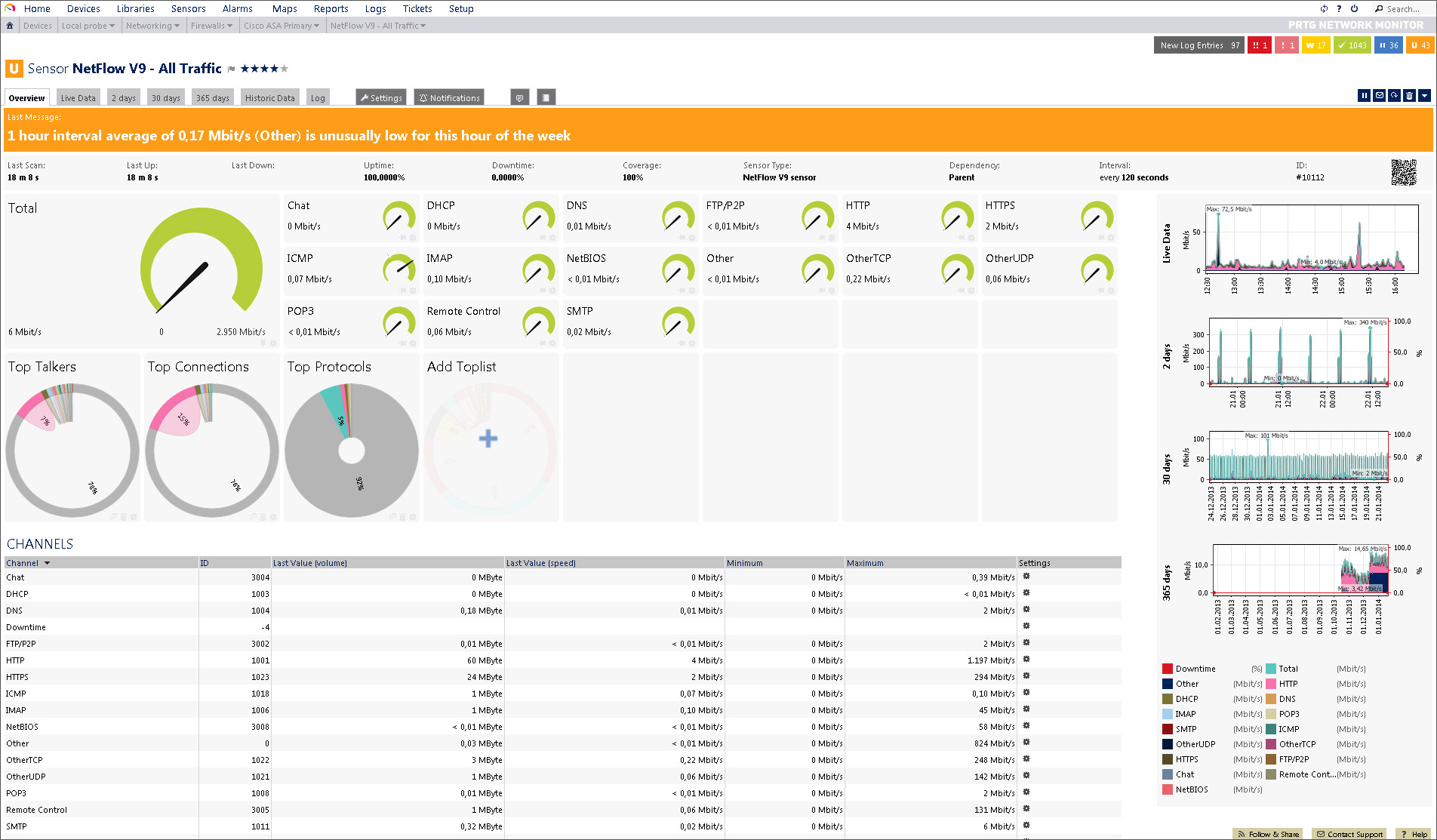
NetFlow is the term given to a network protocol designed by Cisco to collect IP traffic and conduct network monitoring. NetFlow analyzers collect data generated by devices throughout the network and allow the user to view historic and real-time perspectives of the network. To identify suspicious activity that could indicate network infrastructure device compromise, administrators need to perform efficient analysis of the telemetry collected from the network. Analysis tools mentioned in the Instrumentation section of this document can often help in.
At certain times of the day). Intrusion Detection: If you keep getting failed login attempts, it could mean someone is trying to break into your network. Also, sudden spikes in network traffic can indicate an attack. You will only detect these attacks if you are monitoring your network. Network planning: By monitoring your network, you can determine what parts of your network to improve. For example, by keeping an accurate inventory, you will be prepared to change devices that are going obsolete (end-of-life). Also, you can better plan the quality of service (QoS) that should be applied to different kinds of traffic.What must you monitor?It is important to note that while you can monitor all the devices on your network (including workstations), you may not want to.
For example, you may not have the capacity to manage all the data/logs generated by the numerous devices on your network.Ideally, you should monitor the critical devices on your network e.g. The Internet Edge Router/Firewall. For example, it is common practice for banks with several branches/ATM points to monitor the edge devices at those branches to detect when something goes wrong and fix it promptly.In this article, we are going to talk specifically about monitoring Cisco devices including routers (e.g.
Network Infrastructure Design
Windows Network Infrastructure
), switches (e.g. ), security devices (e.g. ) and wireless devices (e.g. ).ProtocolsThere are various protocols that help in network monitoring including:. SNMP: Simple Network Management Protocol operates using an agent-manager model. Can be used to “get” and “set” information and is probably the most used monitoring protocol.: Internet Control Message Protocol is mostly used to determine the reachability of a network device i.e.
Network Infrastructure Diagram
Using ping, although it can provide other information like delay. Syslog: Syslog is used to send logs (e.g. Interface up/down) to a. RADIUS and TACACS+: Even though these two protocols can be used for other things like authentication and authorization, they also provide good accounting (logs) features.
RADIUS is an industry standard while TACACS+ is Cisco proprietary. NetFlow: is a Cisco developed protocol used to.
Comments are closed.